Blog
HPE and AMD deliver exceptional server security features—down to the core
Wednesday, October 06 2021 05:48HPE ProLiant Gen10 Plus servers with AMD EPYC processors are the world’s most secure industry-standard servers. Find out what gives them the capabilities to defend against threats inside and out.
Security is an ever-present concern for every IT professional, and despite the alarming increase in high-profile breaches in recent months, the state of readiness for most companies when it comes to cyber security is lacking. Nearly 80% of senior IT employees and security leaders believe their companies lack sufficient protection against cyber-attacks—despite increased IT security investments made in 2020.[1]
Hackers are becoming more sophisticated with each new wave of attacks, and simply protecting software and networks is no longer enough. Organizations need to take a holistic approach to security that begins with everything that goes into their servers, right down to the silicon.
HPE provides security through the product lifecycle
HPE provides an intelligent, 360-degree view of security that begins at the manufacturing supply chain and concludes with a safeguarded, end-of-life decommissioning:
- Secure supply chain: HPE ProLiant Gen10 Plus server security starts with corruption-free server manufacturing and auditing the integrity of every component, including hardware and firmware—ensuring that the server begins its lifecycle uncompromised.
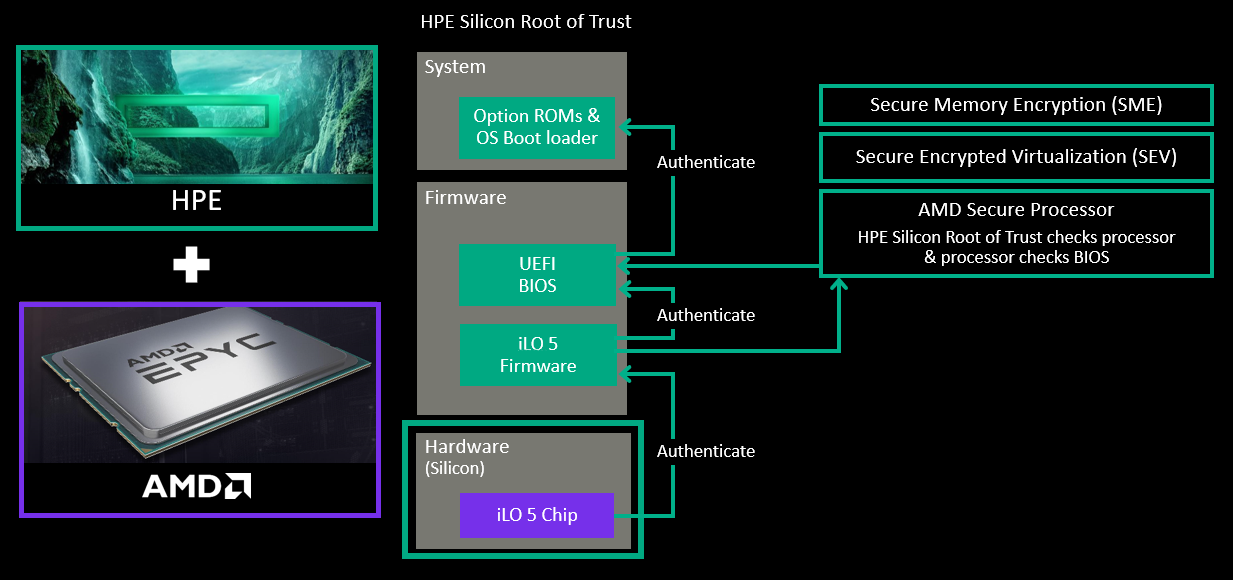
- Silicon root of trust: The HPE-exclusive silicon root of trust anchors the essential firmware of HPE ProLiant Gen10 Plus servers to an HPE-exclusive ASIC even before the server is built, creating an immutable fingerprint for the AMD Secure Processor that must be matched exactly before the server will boot. This ensures malicious code is contained and healthy servers are protected.
- Server configuration lock: Secured by a customer-supplied password, server configuration lock creates a digital fingerprint of the server configuration, preventing it from booting if an unauthorized configuration change or other illicit tampering is detected.
- Security modes: Equipped with HPE Integrated Lights-Out 5 (iLO 5), HPE ProLiant Gen10 Plus servers provide four security modes—production, high security, FIPS 140-2, and the Commercial National Security Algorithm (CNSA) suite, the highest-level cryptographic algorithms available for commercial systems.
- iLO 5 Security dashboard: A single interface displays overall server security status and the current configuration for the security state and server configuration lock, along with the status of numerous other security features. The Security Dashboard also provides security change alerts and manages security settings.
- Server system restores: Should a server become compromised, the fastest path to bringing it back online and into normal operation is with HPE server system restore, a feature of HPE iLO 5. Server system restore provides an automated recovery, including restoration of validated firmware and facilitated recovery of the operating system, application, and data connections.
- One button secure erase: When it’s time to retire or repurpose an HPE ProLiant Gen10 Plus server, one-button secure erase speeds and simplifies the complete removal of passwords, configuration settings, and data, preventing inadvertent access to previously secured information.
HPE 360-degree holistic server security
HPE ProLiant Gen10 Plus servers are the world's most secure industry-standard servers.[2] This claim is based on the unique HPE-exclusive silicon root of trust technology, along with several other differentiating security technologies that are available only on HPE servers with AMD EPYC processors.
HPE silicon root of trust
The HPE silicon root of trust protects against firmware attacks, detects previously undetectable compromised firmware and malware, and, in the event of an attack, helps the server recover rapidly to a known and secure state, with trusted firmware, and without manual intervention.
Available on HPE ProLiant Gen10 Plus servers, the HPE silicon root of trust is based on a hardware-validated boot process, ensuring that only HPE signed firmware will boot, by validating through the silicon root of trust, ensuring that your booted firmware is safe.
This involves an anchor for the boot process rooted in hardware that cannot be updated or modified in any way. When combining this foundation with a cryptographically secured signature, there are no easily accessible gaps for hackers to exploit. If a hacker inserts a virus or compromised code into the server firmware, the configuration of the firmware is changed, creating a mismatch to the digital fingerprint embedded in the silicon.
HPE Integrated Lights-Out 5 (iLO 5)
HPE iLO 5 is a remote server management processor (and firmware) embedded on the system boards of all HPE ProLiant Gen10 Plus servers. iLO 5 includes server management software that enables you to securely configure, monitor, and update your HPE servers seamlessly, from anywhere in the world.
As it initiates, iLO 5 firmware validates the basic input/output system and looks for the “digital fingerprint” of iLO firmware burned into the silicon chip. That immutable fingerprint verifies all the firmware code is valid and uncompromised. If the validation fails at any level, iLO 5 and the HPE silicon root of trust will not allow the server to power on. Because HPE makes its own silicon chip and firmware, it creates a bond that cannot be broken between the two.
The HPE iLO Advanced unlocks more capabilities
Building on iLO 5, HPE iLO Advanced gives you premium security capabilities that protect your HPE servers from attacks and detect intrusions allowing you greater server security through innovations that protect your HPE servers from attack, detect potential intrusions, and allow users to recover their firmware securely.
- Protection: iLO 5 enforces the use of cryptography. Algorithms that confirm to iLO 5 also introduce support for two-factor authentication via Personal Identity Verification (PIV) cards and Common Access Cards (CAC).
- Detection: Runtime Firmware Verification ensures that your essential firmware is checked at regular intervals to identify any potential intrusions that may occur post-boot.
- Recovery: Avoids lasting damage to your business by quickly restoring essential firmware to factory settings, or the last known authenticated safe setting, in the unlikely event of a breach.
AMD EPYC processors featuring Infinity Guard
HPE ProLiant DL3x5 Gen10 Plus servers feature AMD EPYC processors that are designed with a sophisticated suite of security features call AMD Infinity Guard. Built-in at the silicon level Infinity Guard offers the advanced capabilities required to help defend against internal and external threats—all with minimal impact on system performance.
Today, many security threats come from inside the organization. AMD Infinity Guard includes Secure Memory Encryption (SME) that helps protect against attacks on the main memory (such as certain cold-boot attacks) by encrypting the data. High-performance encryption engines integrated into the memory channels help speed performance, and all of this is accomplished without modifications to your application software.
With 2nd and 3rd Generation AMD EPYC™ processors, Infinity Guard helps safeguard privacy and integrity by encrypting each virtual machine with AMD Secure Encrypted Virtualization (SEV), which uses one of up to 509 unique encryption keys known only to the processor. This aids in protecting the confidentiality of your data even if a malicious virtual machine finds its way into your virtual machine’s memory, or a compromised hypervisor reaches into a guest virtual machine.
3rd Gen AMD EPYC processors feature the next layer of SEV called Secure Nested Paging (SEV-SNP). SEV-SNP adds strong memory integrity protection capabilities to help prevent malicious hypervisor-based attacks such as data replay, memory re-mapping, and more, to create an isolated execution environment.
AMD Infinity Guard helps secure the boot process, encrypts the entire main memory with SME, and secures virtualized environments and containers with SEV. Now, with SEV-SNP, 3rd Gen AMD EPYC processor security is stronger than ever, helping to cryptographically isolate and secure more than 500 virtual machines per server.
Why choose HPE ProLiant servers with AMD EPYC Processors?
HPE ProLiant DL3x5 Gen10 Plus servers with AMD EPYC processors deliver peace of mind by helping you protect and grow your business:
- Protect your business: Keep moving at full speed, with 360-degree security solutions for file storage and backup to ensure that your customer’s data is well protected.
- Grow your business: Do more with secure data management and adopt secure virtualization and hybrid-cloud solutions to maximize performance, security, and scale—all while reducing costs.
- Peace of mind: ProLiant servers are tested and validated on a variety of applications and solutions, offering the services, speed, and security that you need.
Find out more
- Help Protect Your Data with HPE and AMD video
- Protect, detect, recover with HPE ProLiant Gen10 Plus and AMD EPYC technology for secure virtualization solution brief
- iLO 5 Chip with Silicon Root of Trust Protects Servers from Attacks video
- 5 Reasons why AMD Infinity Guard matters for security
- Five Questions About SEV video (AMD Secure Encrypted Virtualization)
Tyler Hofstede
Hewlett Packard Enterprise
twitter.com/hpe_compute
linkedin.com/showcase/hewlett-packard-enterprise
hpe.com/servers